Handling Files, Datasources, and the Network
![]() Protecting Datasources from Access via the Windows Explorer
Protecting Datasources from Access via the Windows Explorer
Do not attempt to edit, rename, or move Chromeleon data via the Windows Explorer; this may cause problems with Chromeleon's indexing. To ensure that Chromeleon files are not inadvertently manipulated in the Windows Explorer, hide the Chromeleon datasource structure.
In the Browser
Click the datasource that you want to protect.
Select Properties on the context menu.
On the General tab page, select the Protect Datasource Directory check box.
Only users who have the ModifyProtectionMode Privilege are authorized to clear this check box. Therefore, to prevent other users from clearing this check box, make sure that they do not have the ModifyProtectionMode privilege. (The administrator assigns and removes this privilege in the User Manager (CmUser program).)
The Protect Datasource Directory check box is selected by default when you create a new datasource or when you remount a datasource. Nevertheless, you can select this check box later for existing datasources and/or for datasources that are already mounted. Changes become active only after the logged-on user has logged off in Windows or after you have restarted the operating system.
For a datasource that has been protected in this way, the directory structure is hidden in the Windows Explorer and in Windows file dialog boxes. A Chromeleon icon is displayed instead, indicating that the datasource is protected:
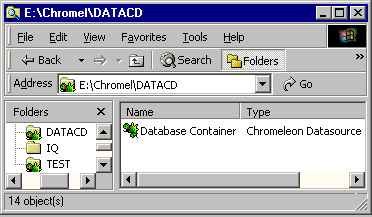
![]() Tip:
Tip:
Double-clicking the Chromeleon icon in the right pane of the Windows Explorer starts the Chromeleon client.
In the User Manager (Transaction Agent)
When the Transaction Agent is implemented, users are prevented by the Windows operating system from accessing the part of the datasource in the file system; all Chromeleon transactions are conducted via the Transaction Agent account. This ensures that all transactions on Chromeleon data can be performed only through Chromeleon programs, and provides a much higher level of data security than the protection mechanism described above.
Enable the Transaction Agent in the User Manager (CmUser program). For more information, refer to Chromeleon User Management ![]() Setting up the Transaction Agent.
Setting up the Transaction Agent.